Study Bay Coursework Assignment Writing Help
Introduction:
The rapid development of various communication and wireless technologies had led to ultimate spectrum insufficiency. This may cause a great spectrum extinction thereby not allowing new wireless services to be installed. To overcome this great spectrum disaster and to optimally use the underutilized bands, a new technology so called cognitiveradio evolved. This technology scampers the software programs thereby helps cognitive user to look for spectrum holes, pick the best among them, work jointly in coordination with other users and do not disturb the owner of spectrum on arrival[1].The members do stay connected in an ad-hoc manner and there is no guaranteed network architecture. This makes the privacy issues more intricate than in conventional wireless devices. [2]. The medium of transport is free air, any adulteration of data can be done without much being noticed by the sufferer and at the worst case, the data signals are even jammed. Establishing security in these networks is a risky task because of its inimitable quality. [4] The innate temperament of it has made it an open play ground for attackers.
There are four layers in a cognitive network out of which Physical layer is the lowermost layer and various attacks are feasible here .The main focus is on attacks in these layers since it is the common layer and has same compatibility with all other devices. The rapid development of technology has led to a new attack so called Primary User Emulation Attack wherein the imitation of spiteful user as a primary transmitter occurs to deceive the secondary users and gain access over the white space.
Better functioning of the Cognitive network is affected to a great extent if this Primary User Emulation Attack is severe.[3]Earlier methods and the most primitive are cyclostationary and the energy detection ones [11]. The first technique is based on the fact that the signals from primary users are periodic and do have regular cyclostationarity property. The second method involves comparison of energy level of the signal with a preset threshold. [10].These methods are already bypassed owing to the rapid growth of technology. It can be done either by impersonating the primary transmitted signal or high power signal to confuse the energy detector [9].
Thus to avoid the problem of PUEA, we need a trustable method to verify the arrival of primary user .One such method is verification of licensed user by means of biased reaction signalling[6]. The other technique involves LocDef , where we use localization technique by non interactive technique [7]. We can also use Public encryption systems thereby ensuring the trustworthy communication[5]. Primary user has a closely placed helper node which plays the role of a bridge thereby enabling of the verification of the primary user’s signals using cryptographic signatures and authentic link signatures.[8].There are hand off techniques meant for secret communication of sharing session keys between the client and the router [12].
We do add the tag for authentication in a transparent way so as no to interfere with the primary receiver but still maintain authenticity with the cognitive user. We can add this tag in parity bits of the codeword or in the modulation scheme .[13].But to make this signature embedding accurate, error control codes like convolutional codes, turbo codes or alamauti codes can be used. .A convolutional encoder is a linear predetermined-state device with n algebraic function generators and K stage shift register. The binary input data, is shifted as b bits at a time along the registers. Decoding can be done by either sequential decoding, maximum likelihood or feedback decoding[15]. In case of turbo codes, two RSC elementary codes are in a parallel organization. Maximum A Posteriori algorithm is used for decoding it in iterative process[16].In a highly noisy environments single error control codes do not have high coding gain. In order to improve this concatenated codes are preferred.[14] Hence to cope up with the FCC regulations, we proposed a method in which the authentication tag is embedded onto the data signal by the helper node after encoding and the comparative study of which concatenated codes serve the best to reduce the bit error rate has been discussed.
II. PROPOSED METHOD:
2.1)HASH ALGORITHM:
Procedure:
Message is Padded in such a way that the length of message matches to 896 modulo 1024 . In certain cases ,the length may match yet the padding becomes additional. We do add a binary bit 1 followed by binary 0s to make the desired length. Depending upon the actual message size, we may have n number of bits padded where n=1 to 1024.We do assume that the message after padding is an unsigned integer of 128 bits and output of earlier two steps is a 1024 bit integer in order to calculate the length of message. Eight registers each of capacity to hold 64 bits (p, q, r, s, t, u, v, w) are needed to grasp the 512 bit results momentarily .This 512 bit output is carried over as an input to the consecutive stages. For the first stage, the previously stored transitional hash output is taken. On processing the padded message of 1024 bits, we get 64 bit as input per round. So to maintain the security and avoid repetitions, we do use a constant to point to the round number out of 80.After completion of 80 rounds, the final stage result is fed back to the first block until the message gets over. Thus we need (Oi-1) to produce Oi where I is the stage number.
2.2)METHOD OF EMBEDDING:

We assume that the primary transmitter and the helper node share almost the same geological location and the helper node has a secret communication with the secondary users there. The primary transmitter on arrival generally transmits a data signal to its intended primary receiver. Since the primary transmitter has the highest priority and in no way it should be interfered we use the helper node to embed this security tag. The primary transmitter encodes the data sequence, modulates and transmits the signal. The data sequence after encoding is modulated and being transmitted by the primary transmitter. The helper node here repeats the signal and the hashed output is being embedded by it .Here the embedding is done in such a way that the tag to data ratio is comparatively low. Encode the data sequence to form N code words and each codeword contains p bits. We get an authentication tag by splitting the hash function output obtained earlier into p bit blocks. The tag thus obtained is substituted in the place of first p bits of the total N code words obtained. We do obey the regulations as per FCC since this tag embedding task is solely performed by the helper node. At the receiver end the authentication tag is retrieved and checked for authenticity. This tag verification is being done by the Cognitive Radio user upon reception since we did assume that the key for hash had been exchanged privately earlier. If verification is successful, the task is suspended and secondary user looks for any new white space.
BLOCK DIAGRAM:













RESULTS AND DISCUSSION:
BER VALUES FOR CONVOLUTIONAL CODES:
|
Eb_N0 |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
Before embedding |
10323 |
8506 |
6713 |
5111 |
3611 |
2440 |
1463 |
788 |
361 |
|
After embeddin |
10324 |
8511 |
6720 |
5118 |
3613 |
2445 |
1465 |
791 |
363 |

BER VALUES FOR TURBO CONVOLUTIONAL CODES:

|
Eb_N0 |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
Before embedding |
10201 |
8385 |
6645 |
5065 |
3602 |
2428 |
1435 |
732 |
340 |
|
After embeddin |
10264 |
8530 |
6793 |
5210 |
3716 |
2460 |
1484 |
750 |
342 |
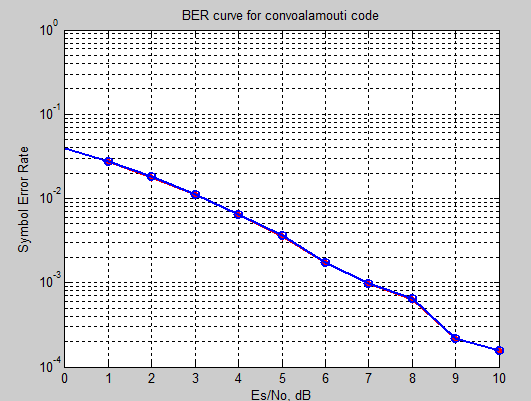
BER VALUES FOR CONVOLUTIONAL-ALAMOUTI CODES:
|
Eb_N0 |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
CONVO-ALAMOUTI before embedding |
6114 |
4879 |
3609 |
2639 |
1778 |
1153 |
740 |
410 |
252 |
|
CONVO- ALAMOUTI after embedding |
6120 |
4883 |
3617 |
2645 |
1783 |
1160 |
743 |
441 |
254 |
BER VALUES FOR TURBO-ALAMOUTI CODES:

|
Eb_N0 |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
TURBOALAMOUTI before embedding |
6049 |
4815 |
3572 |
2618 |
1690 |
1124 |
724 |
395 |
249 |
|
TURBO- ALAMOUTI after embedding |
6055 |
4823 |
3580 |
2635 |
1695 |
1135 |
728 |
398 |
251 |
REFERENCES:
- O. León ,Hernández-Serrano, J.,Soriano, M.,. Securingcognitiveradionetworks, International Journal of Communication Systems,23: 633-652. May 2010
- Parvin, S.
 ,Han, S.
,Han, S. ,Tian, B.
,Tian, B. ,Hussain, F.K, Trust-based authentication for secure communication inCognitiveRadioNetworks,International Conference on Embedded and Ubiquitous Computing, Hong Kong; China;,pp. 589-596. December 2010.
,Hussain, F.K, Trust-based authentication for secure communication inCognitiveRadioNetworks,International Conference on Embedded and Ubiquitous Computing, Hong Kong; China;,pp. 589-596. December 2010.
- Zhang, C.,Yu, R.,Zhang, Y., Performance analysis of Primary User Emulation Attack inCognitiveRadionetworks,International Wireless Communications and Mobile Computing Conference,pp.371-376. August 2012.
- Parvin, S.,Hussain, F.K.,Hussain, O.K.,Han, S.,Tian, B.,Chang, E., Cognitiveradionetworksecurity: A survey ,Journal of Network and Computer Applications, 35: 1691-1708. November 2012.
- Parvin, S.,Hussain, F.K.,Hussain, O.K, Digital signature-basedauthenticationframework incognitiveradionetworks, International Conference on Advances in Mobile Computing and Multimedia,pp.136-142. December 2012.
- Kumar, V.,Park, J.M.,Kim, J.,Aziz, A., Physical layerauthenticationusing controlled inter symbol interference, International Symposium on Dynamic Spectrum Access Networks,pp. 286. October 2012.
- Ruiliang Chen, Jung-Min Park, and Jeffrey H. Reed,Defense against Primary User Emulation Attacks in Cognitive Radio Networks,IEEE transactions on Selected areas in communication,26:25-37. January 2008.
- Tingting Jiang., Huacheng Zeng., Qiben Yan., Wenjing Lou.,Thomas Hou,Y, On the Limitation of Embedding Cryptographic Signature for Primary Transmitter Authentication, IEEE transactions on Wireless communication letters,1:324-327. August 2012.
- Chen,R.,Park,J.,Reed,J.H, Defense against primary user emulation attacks in cognitive radio networks, IEEE transactions on Selected Areas in Communications, 26:25–37. 2008.
- Liu,Y.,Ning,P., Dai,H, Authenticating primary users’ signals in cognitive radio networks via integrated cryptographic radio networks via integrated cryptographic and wireless link signatures,IEEE Symp. on Security and Privacy, pp. 286–301. 2010.
- Kim,H.,Shin,K.G, In-band spectrum sensing in cognitive radio networks: energy detection or feature detection? ,ACM international conference on Mobile computing and networking, pp.14-25. 2008.
- He, Y.,Xu, L.,Wu, W., A local joint fast handoff scheme incognitivewireless mesh networks , IEEE transactions on Security and Communication Networks, 7:455-465. February 2014.
- Xi Tan., Kapil Borle., Wenliang Du., Biao Chen, Cryptographic Link Signatures for Spectrum Usage Authentication in Cognitive Radio, ACM conference on Wireless network security,pp.79-90.2011.
- Avila, J.,Thenmozhi, K, DWT highlighted concatenated multi band orthogonal frequency division multiplexing (MB-OFDM)-upgraded enactment, International Journal of Engineering and Technology,5:2155-2162. June 2013.
- Andrew J. Viterbi, Convolutional Codes and ’Their Performance in Communication Systems , IEEE transactions on Communication Technology,19:751-772. October 1971.
- Claude Berrou., Alain Glavieux ,Near optimum error correcting coding and decoding-turbo codes,IEEE Transactions on communications,44:1261-1271. October 1996
- Wang,X.,Wu,Y.,Caron,B, Transmitter identification using embedded pseudo random sequences, IEEE Transactions on Broadcasting,3:244-252. September 2004.
- Danev,B.,Luecken,H.,Capkun,Z.,Defrawy,K.E,Attacks on physical-layer identification,ACM Conference on Wireless Network Security,pp.89-97. 2010.
- Proakis,J.G., Salehi,M, Digital Communications.New York, McGraw-Hill, pp. 192, 434, 472-474. 2007.
- Chen,Z.,Cooklev,T.,Chen,C., Pomalaza-R´aez,C, Modeling Primary User Emulation Attacks and Defences in Cognitive Radio Networks, International Performance Computing and Communications Conference,pp.208-215. 2009.
